From early white-paper sketches to today’s multi-billion-dollar ecosystems, sidechains have evolved into one of the most versatile instruments for expanding blockchain capabilities.
Origins and Conceptual Framework
The Scalability Dilemma in Early Blockchains
When Bitcoin launched in 2009 and Ethereum followed in 2015, both networks soon encountered a now-famous bottleneck: every full node had to re-execute every transaction, capping throughput at a few dozen transactions per second for the sake of decentralization. As global adoption accelerated, mempools clogged, fees spiked, and users demanded a technical off-ramp that preserved core security while lifting hard limits.
Birth of the Sidechain Idea
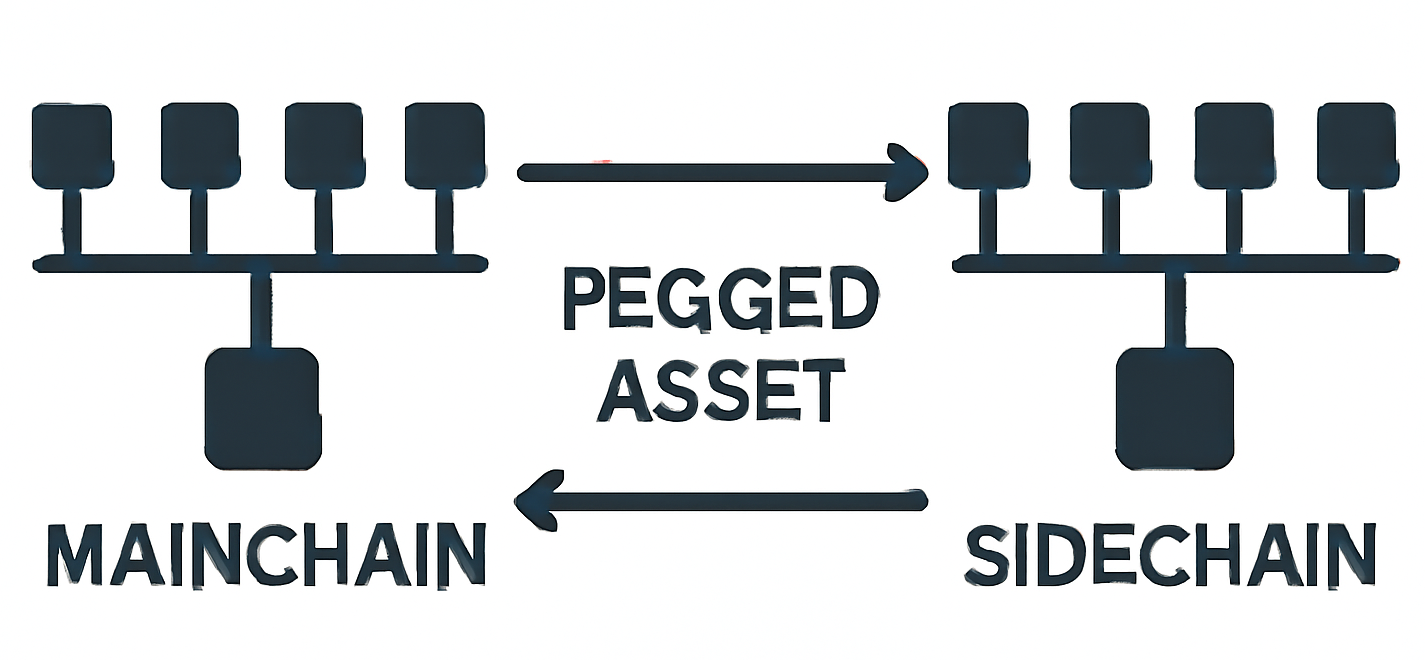
In 2014, researchers from Blockstream issued a paper describing a secondary blockchain—linked to the mainchain through a cryptographic two-way peg—where assets could move freely without altering the parent network’s consensus rules. The proposal promised a sandbox for experimentation, enabling new opcodes, faster blocks, or privacy features, all while allowing users to “retreat” to the safer mainnet when desired.
How Sidechains Work Under the Hood
Two-Way Peg Mechanisms
The beating heart of any sidechain architecture is the bridge that shuttles value across ledgers. Broadly, three models dominate:
| Peg Model | Custody Location | Typical Finality Time | Example Networks |
|---|---|---|---|
| Federated Multisig | Key-holding federation | Minutes to hours | Liquid, Rootstock (early) |
| SPV-Based (Simplified Payment Verification) | Smart contracts on each chain | ~6 mainchain blocks | tBTC (v1), PowPeg RSK |
| Light-Client Bridge | Decentralized relayers & proofs | Seconds to minutes | Polygon zkEVM, NEAR Rainbow |
Consensus Algorithms Inside Sidechains
Since a sidechain sets its own consensus rules, designers often swap the base layer’s energy-heavy Proof-of-Work for more flexible engines. Popular picks include:
- Proof-of-Stake (PoS)—validators lock capital to propose blocks, gaining speed and energy savings.
- Delegated Proof-of-Stake (DPoS)—token holders elect a smaller validator set, trimming block times to sub-seconds.
- Practical Byzantine Fault Tolerance (pBFT)—nodes use rounds of voting for instant finality, ideal for enterprise settings.
Security Models and Trust Assumptions
An elegant sidechain never compromises the parent chain’s settlement guarantees. Yet, because validators differ, attack surfaces shift from hash-power economics to governance failures, key collusion, or bridge software bugs. Builders therefore publish formal audits and often cap the total value locked (TVL) during beta phases.
Technical Building Blocks
Bridges and Relays
Every bridge maintains three core components:
- Lock Contract—escrows mainnet coins.
- Relay—feeds light-client proofs across chains.
- Mint/Burn Logic—creates or destroys sidechain representations (“wrapped” tokens).
Smart-Contract Oracles
Data such as price feeds, block headers, and Merkle proofs must hop between worlds. Oracles like Chainlink or Band connect to bridge contracts, providing cryptographically signed attestations that allow trust-minimized asset migration.
Federated vs. Decentralized Validators
A federated peg delegates signing authority to a fixed committee—simpler to launch but arguably more censorable. Decentralized validators, by contrast, run permissionless nodes and stake capital, aligning economic penalties with honest behavior.
Prominent Sidechain Implementations
Rootstock (RSK) for Bitcoin
RSK links BTC to an EVM-compatible chain running 30-second blocks. A hybrid “PowPeg” combines Bitcoin-merge-mined hash power with a 15-of-20 multisig federation, allowing Bitcoiners to deploy Solidity contracts without leaving the broader Bitcoin security umbrella.
Polygon PoS Chain for Ethereum
Launched in 2020, Polygon’s PoS sidechain batches EVM transactions and checkpoints them back to Ethereum, achieving ~7,000 TPS. A value-staking validator set handles blocks while a Plasma-inspired bridge enables token transfers.
Liquid Network by Blockstream
Liquid targets exchanges and OTC desks needing rapid settlement of large Bitcoin transfers. Its 1-minute block time and confidential transaction format mask amounts, while a 15-of-15 dynamic federation secures assets.
Use Cases Beyond Scalability
Tokenization and Asset Issuance
Sidechains let projects issue stablecoins, security tokens, or in-game items without bloating L1 fees. For instance, Tether’s USDt circulates on Liquid with confidential asset tags that obscure balances.
Privacy-Enhanced Transactions
By experimenting with cryptographic primitives like Mimblewimble or zk-SNARKs, sidechains deliver opt-in privacy while keeping the transparent mainnet untouched.
Domain-Specific Functionality
Gaming studios crave sub-second finality and cheap NFTs; DeFi builders need lower gas costs for complex swaps; supply-chain consortia want enterprise permissioning. Sidechains provide each niche a tailor-made environment.
Interaction Between Mainchain and Sidechain
Depositing Assets to the Sidechain
User sends 1 BTC to a lock script on mainnet. After sufficient confirmations, a relay proves the deposit to the sidechain, where 1 “rBTC” is minted. From the user’s view, the bridge appears as a single UI step, but under the hood dozens of cryptographic messages pass between light-clients.
Withdrawing Back to the Mainchain
Conversely, burning sidechain tokens triggers a withdrawal proof. Once the mainnet contract verifies signatures and SPV proofs, the originally locked BTC is unlocked. Some networks add challenge periods to let watchers dispute fraudulent claims.
Economic and Incentive Considerations
Fee Structures
Gas fees on sidechains trend lower than on congested L1s, yet bridge costs—especially withdrawal gas—can spike during mainnet surges. Many wallets show blended estimates so users aren’t blindsided.
Validator Rewards
Stakers earn newly minted sidechain tokens, a cut of gas, or even rebated mainchain coins, creating a parallel economy that—if mis-aligned—may incentivize “sidechain maximalism” at L1’s expense.
Impact on Mainchain Value Accrual
Far from cannibalizing, sidechains often increase demand for the base asset by adding new utility and locking coins out of liquid circulation during bridging.
Developer Perspective
Tooling and SDKs
Frameworks like Truffle, Hardhat, and Brownie remain compatible with most EVM sidechains. RSK’s “lumino” micro-payment channels and Polygon’s Edge SDK let teams spin up custom PoS chains in hours.
Testing and Deployment Strategies
Teams typically maintain three instances: a private fork for unit tests, a public testnet mirroring bridge contracts, and mainnet for production. Continuous integration scripts automatically re-deploy contracts to each environment upon commit.
Interoperability Standards
Proposals like EIP-3220 (Meta-Transaction Envelope) or Bitcoin’s OP_CTV aim to standardize user flows so wallets can abstract away cross-chain complexity.
Case Studies in Production
| Network | Mainchain | Peg Type | Consensus | Avg TPS | TVL (USD) |
|---|---|---|---|---|---|
| RSK | Bitcoin | PowPeg (SPV + Federation) | Merge-mined PoW | 100+ | $400M |
| Polygon PoS | Ethereum | Checkpoint/Merkle | PoS (100 validators) | 7,000 | $6B |
| Liquid | Bitcoin | Federated Multisig | Strong Federations | 1,000 | $350M |
| Gnosis Chain | Ethereum | Light-Client Bridge | xDai PoS | 2,000 | $300M |